The Internet is like a deep ocean. As an experienced Internet user, you can swim in its depths without any problem. However, not every user is aware of the threats and bad actors that are waiting in the shallow water. Nowadays, hackers are primarily financially motivated. Therefore, they are constantly coming up with new methods to get their hands on some money. One of their favorite methods is tricking others into sending them money directly, expose their credit card information, credentials, or even provide the hackers with remote access to their devices. This method is called phishing, and in this blog post, we will look into how they take advantage of users selling their stuff on marketplaces.
We probably all owned something that we felt was too good to be thrown out, but we did not have any use for it anymore. A great solution is to advertise such goods in an online marketplace. Someone may buy it and make use of it, and we get some of our money back. So, you got your old iPhone, took photos of it, placed an advertisement on your local marketplace, and now you wait for your customers. However, not everyone that contacts you wants to make a square deal. We tried to get in touch with some shady characters that want to steal your money by placing advertisements on numerous marketplaces in various countries. Here are our findings.
Initial contact
Scammers contacted us in almost every case via messaging application WhatsApp. Two times they emailed us a question to reach them on WhatsApp. The reason why they are using this app, and not something else like Viber or Telegram, is that WhatsApp is the world's most popular messaging app, so the probability that the victim will be using it is significantly higher. Also, we noticed that they often use WhatsApp Business Account. This is probably because WhatsApp Business allows them to use multiple features (label chat, quick replies, etc.) that make it easier to manage chats with hundreds of potential victims.
The communication
Scammers are trying to deceive you by keeping the communication as believable as possible. The first message was always a question whether the product was still available.
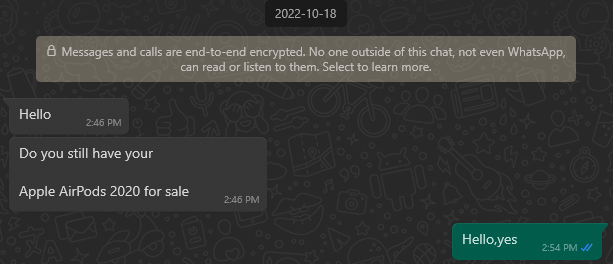
After confirmation, they usually asked for the price. We noticed that they never negotiated the price. They accept anything you send them. They don't want to lose you by messaging you anything that would make you stop communicating with them.
When the price is confirmed, they will continue arranging the item's delivery. We've seen that some scammers are not waiting for anything and offer courier pickup. Others show the desire to meet up but immediately refuse to do so because of their busy schedule.
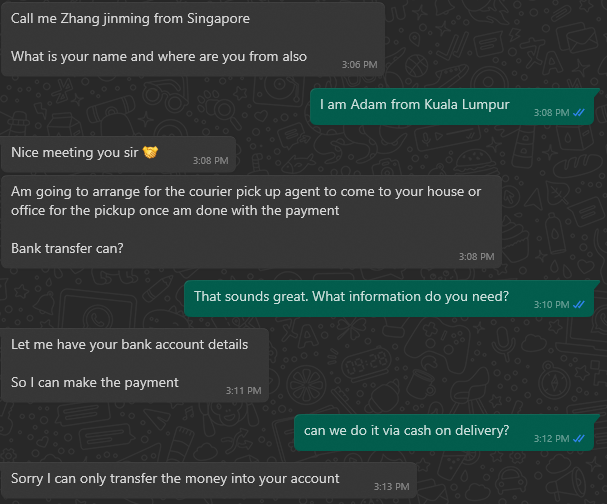
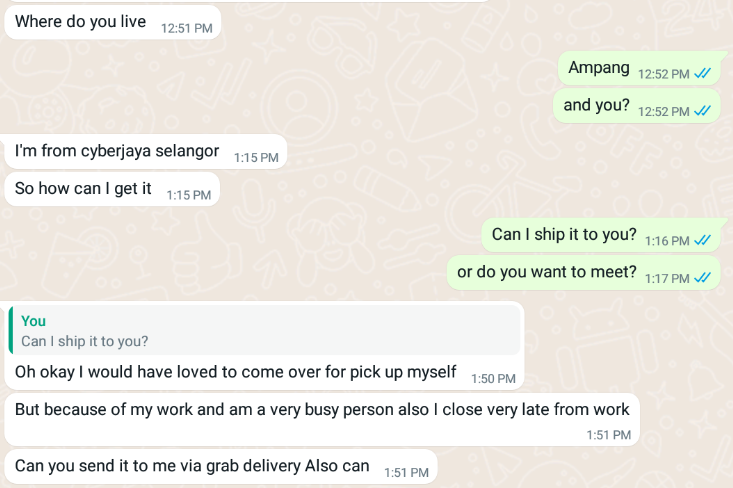
After that, they will ask you to send them your personal information, namely full name, phone number, and address, so they can arrange the courier pick up. When they receive your data, they send you a link to a fake page that tries to imitate delivery companies like DPD, DHL, or some local post service, depending on your country.
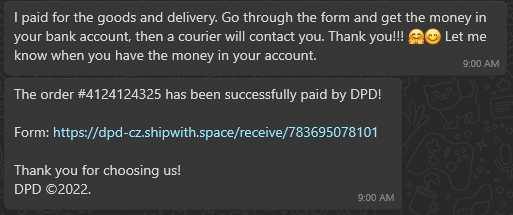
On the web page, you are required to fill in your bank account details "to be able to receive the payment." However, as the web page is fake and you are giving out your internet banking credentials to the scammer, in the meantime, he or she is logging into your internet banking. After they insert your credentials, the fake web page challenges you to confirm a push notification on your phone to receive your money. Actually, you are letting the scammer into your internet banking. This way, they are bypassing your Two-Factor Authentication. And you let them in. At this point, when they have access to your bank account, they can do whatever they want. He or she can transfer your savings or take out a loan and wire it to their account. All they need is to make you confirm one more push notification. According to our experience, most people this far into the transaction do not hesitate to take action because they believe they will receive their money. Still, unfortunately, they just end up with a cleaned-up bank account.
What makes this type of phishing so successful is the fake web page. We have seen some well-crafted fake pages that even us, cybersecurity experts, had a tough time recognizing from real ones. That is apart from a suspicious domain name.Therefore, we do not expect most Internet users to distinguish them from genuine websites and not get scammed.
Fortunately, Whalebone can help you with protecting your customers by providing them with a zero-disruption security. Our solution works on the DNS level and uses AI/ML-driven next-generation threat intelligence, which helps us to keep up with malicious actors.



